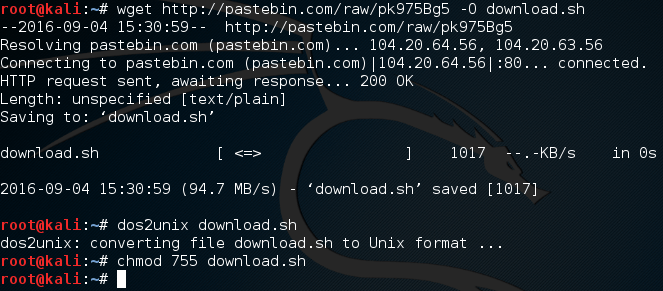
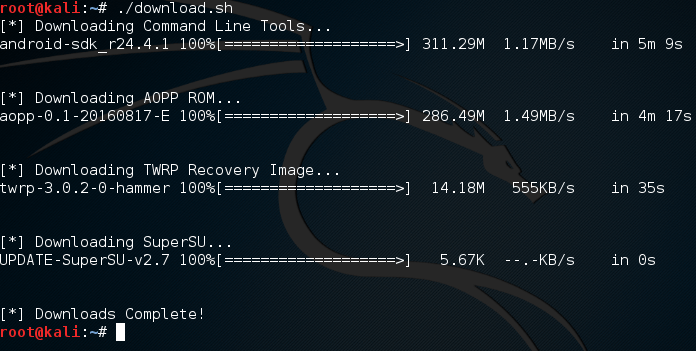
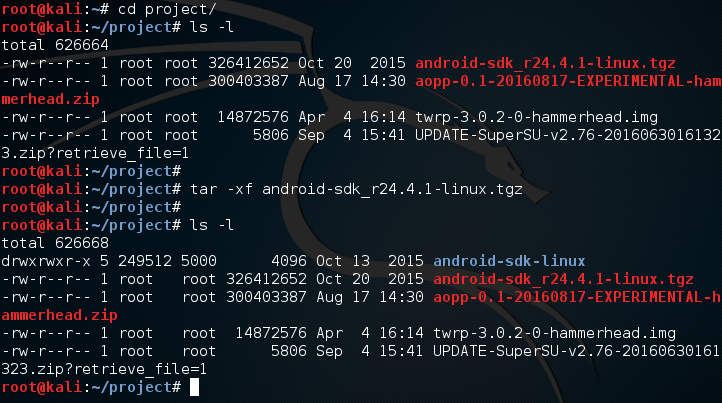
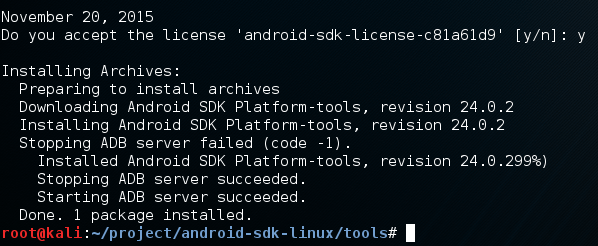
Welcome back everyone, lets talk about DoS attacks and hping3! DoS attacks are some of, if not the, most common attack (DoS stands for Denial of Service). Not to be confused with DDoS, a DoS attack is when a single host attempts to overwhelm a server or another host. This is done by expensing all resources, so that they cannot be used by others.

There is a tool by the name of hping3 that allows the attacker to craft and send custom packets. This allows us to do many things with it including recon, possibly some basic exploitation, but for now we’re going to use it to launch a DoS attack. There are mutliple kinds of DoS attacks, but today we’re going to launching a SYN flood. This sends requests to a server as fast as it can. When these requests are processed, it will take up the server’s resources, and will render it unable to respond to any actual users trying to use it.
The problem with DoS attacks is that when we send all these packets the server, it has our address in it. All the administrator has to do is look at the logs and turn our address into the authorities, then we’re behind bars in a matter of days. We’re not only going to be launching a SYN flood, but we’re going to spoof our address so we don’t get thrown in the big house! Before we launch the attack, let’s deeper discuss the concept of SYN flooding.
SYN Flooding
As we previously stated, a SYN flood is sending an insane amount of requests to a server in order to use up all it’s resources. But you may be asking “What does SYN have to do with using up resources?“. Well, it’s all about the TCP three-way handshake.
If you haven’t already read the second recon article, I suggest you do so in order to understand the TCP three-way handshake. Remember, SYN stands for synchronize. When we send a SYN packet, we’re requesting to establish a connection.
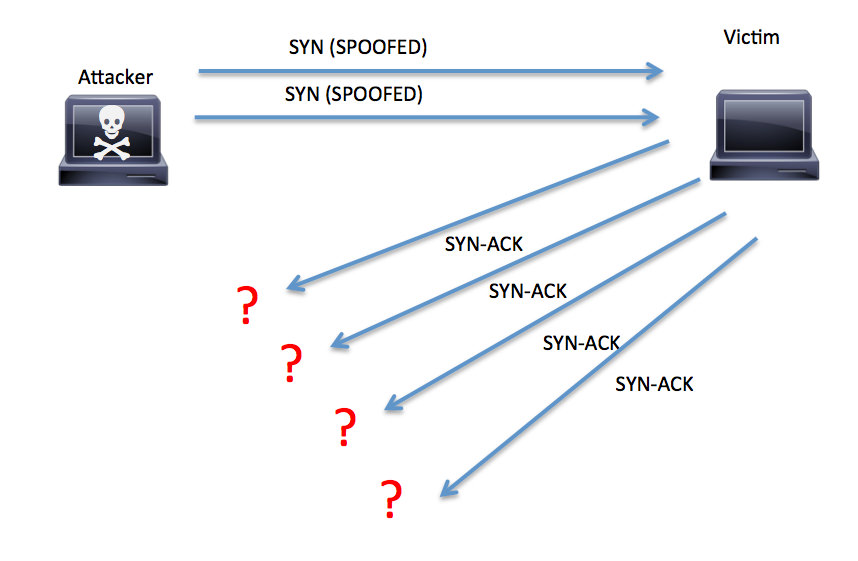 We can see that the attacker sent many SYN packets (with spoofed addresses) to the victim. The victim responded with a SYN-ACK to confirm the connection, but since there was no response, it sends it again and again, using up all it’s resources! Also, since the attacker used a fake address, the administrator will have a much more difficult time tracing the source of the attack.
We can see that the attacker sent many SYN packets (with spoofed addresses) to the victim. The victim responded with a SYN-ACK to confirm the connection, but since there was no response, it sends it again and again, using up all it’s resources! Also, since the attacker used a fake address, the administrator will have a much more difficult time tracing the source of the attack.
Now that we know how SYN floods work, let’s get to launching the attack!
Launching the DoS Attack
First things first, we’ll need to look at the help page for hping3. In order to condense the output, I’m going to grep the lines that are essential. Let’s see the flags we need to use:
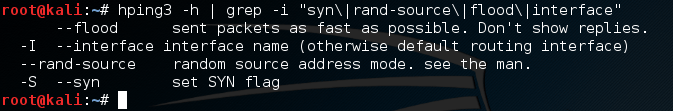
We can see here that we need to use –flood, –interface, -S, and –rand-source. These flags are fairly self-explanatory, but let’s run through them. Using –flood will set hping3 into flood mode. This is the flood part of our SYN flood. Then we have –interface, so we can decide which network interface to send our packets out of. Finally we have –rand-source, this will randomize the source address of each packet. Not only will source not point back to us, but it will appear to come from a wide range of addresses, this increases the trace difficulty even further.
Now that we know what flags we’re going to use, let’s launch our attack. I’m going to be launching this attack against a VM I’ve set up, Metasploitable 2. First, let’s ping the Metasploitable VM to make sure it’s up and running, then we’ll ping it again when we launch our attack to see the effect. Let’s ping it now:
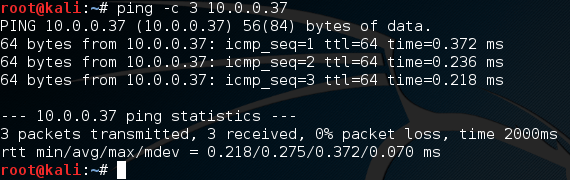 Alright, our VM is up and running. Now let’s take a look at the command we’ll use to launch our attack before we do it:
Alright, our VM is up and running. Now let’s take a look at the command we’ll use to launch our attack before we do it:
Alright, now that we have our command let’s execute it. Now that we’ve started the attack we should see some output like this:
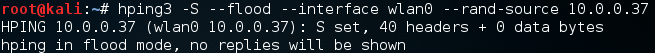
There we go! Now we’re flooding the target. To see our spoofed packets in action, let’s open up one of the best network sniffers out there, wireshark. We should be able to see packets from multiple addresses being flooded towards the same address. Let’s take a look at the packets the wireshark has captured:
 Here we can see 5 packets, each with it’s own unique source address! We can see that they are being send to our target at the IP 10.0.0.37, with the SYN flag set. Now that we’re attacking our target, let’s retry pinging the target and see what happens:
Here we can see 5 packets, each with it’s own unique source address! We can see that they are being send to our target at the IP 10.0.0.37, with the SYN flag set. Now that we’re attacking our target, let’s retry pinging the target and see what happens: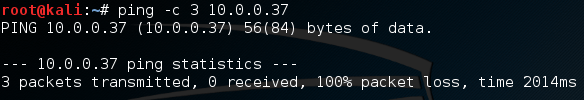 We can see by this ping tool output that our pings failed, we can’t reach the server anymore! This proves that our attack was effective in that the server spent all it’s resources responding to our attack instead of the real users, we’ve successfully DoS’d our target!
We can see by this ping tool output that our pings failed, we can’t reach the server anymore! This proves that our attack was effective in that the server spent all it’s resources responding to our attack instead of the real users, we’ve successfully DoS’d our target!
Since we’ve randomized the source of every packet, it will be much more difficult for an administrator. Now we can launch DoS attack without landing ourselves a seat in prison!
I know this tutorial isn’t really related to any of my currently running series such as the recon series. But due to the recently published article on DoSing with LOIC I felt like this was necessary so if anyone does decide to use this power for evil they won’t land themselves in prison. I’m just looking out for my fellow hackers! The next article will be the start of a brief course teaching the basics of Python, I’ll see you there!
DISCLAIMER: hottechtips.blogspot.com does not condone the use of these tools for illegal activities, we’re just here to educate!